Dynamic Vlan Assignment Microsoft Nps Server
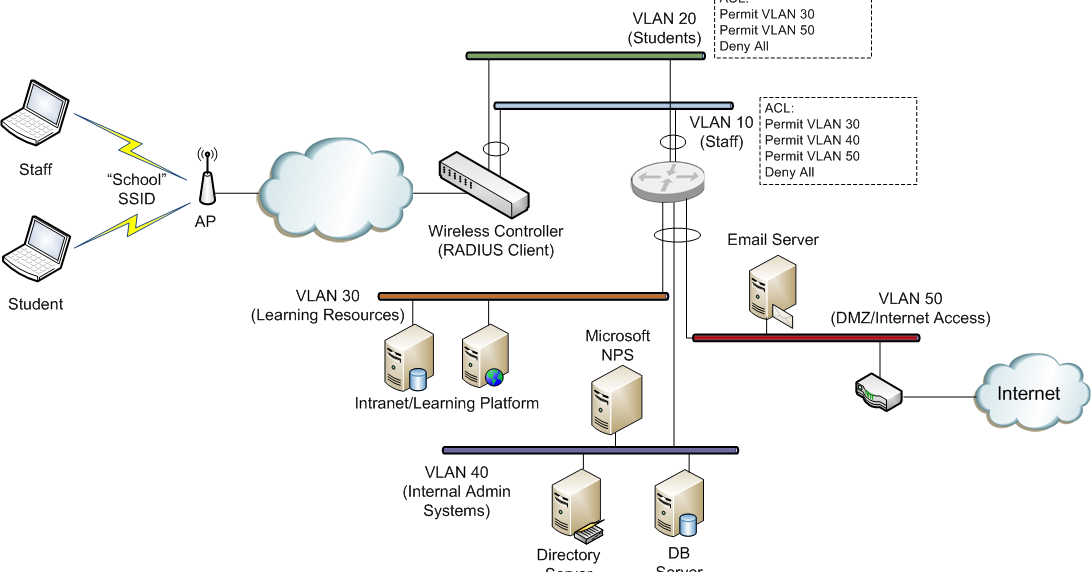

Aug 19, 2008 Network Access Protection Using 802. Manvantara Serial Title Song Mp3 Free Download. 1x VLAN’s. Our NPS server). To support the ability to do dynamic VLAN assignment and not all switches and.
Hoping BudMan can help me out! I have a client who's network is divided (with VLANs) by floor in their building.
With dot1x authentication enabled all users are leasing an IP address from the first DHCP pool regardless of how the port is tagged. So for instance, VLAN 700 is the 2nd floor VLAN.
A user on the 3rd floor connects to a port tagged for VLAN 720, they authenticate through NPS and then receive an IP address from 700. (DHCP is installed on the NPS server) Everything I have found online about 802.1x VLAN assignment suggests that you can assign a VLAN during authentication, but I haven't found anything that would help me tell the server which DHCP scope to lease addresses from based on how the port is already tagged on the switch. If there is a way to do this I would appreciate a nudge in the right direction.
The environment is all Cisco 3750X switches with Server 2012 R2 for NPS and DHCP. I'm thinking the way they have this network set up is not a supported way to accomplish this, but I need to know for sure. They are talking about using sticky-mac if they can't figure this out and I cringe at the thought of all the help desk issues that is going to cause. Yes you can assign vlan based upon auth, so that users get put in whatever vlan you want that user/machine in.
Are you hard coding your switch ports? Can you post a config of one of your switch ports that is tagged for vlan 720?
Why would you tag an access port? You using the term tagged to refer to that is the native vlan of the port? Have you looked at Yes I am hard coding the ports. Here is a port for example (third floor is the same, just 720): interface GigabitEthernet1/0/14 description '2F Wired Workstation' switchport access vlan 700 switchport mode access switchport voice vlan 217 authentication host-mode multi-host authentication port-control auto authentication periodic authentication timer reauthenticate 4800 dot1x pae authenticator dot1x timeout quiet-period 30 I have been on that Cisco support site and it doesn't seem like what I'm trying to do is possible, but I wanted to check with other people who may have experience with dot1x. When configured on the switch and the RADIUS server, 802.1x authentication with VLAN assignment has these characteristics:? If no VLAN is supplied by the RADIUS server or if 802.1x authentication is disabled, the port is configured in its access VLAN after successful authentication.
Recall that an access VLAN is a VLAN assigned to an access port. All packets sent from or received on this port belong to this VLAN. This tells me that the ports should be coming up in the correct access VLAN as assigned on the switchport. However, they are not. Ports configured for switchport access vlan 720 are coming up on VLAN 700 after authentication.
If I remove authentication they of course come up on the correct VLAN as assigned. The only other configuration oddity I see is in vCenter.
The vSwitch servicing the NPS/DHCP server is not a distributed switch and is tagged only for VLAN 700. Does anyone have any vSphere networking experience and can tell me if that would cause the RADIUS packets to come back tagged with the wrong VLAN? What are you doing with the switches in in esxi/vshpere - they can be 0 untagged or the tag of the vlan you want 1-4094 and or 4095 which is trunked. Alif Laila Complete Serial Free Download there. See the attached image. It looks like we're tagging VLAN 700. The port from the switch is trunked with all the necessary VLAN's allowed. This is a setup that I have fallen in on and to me this does seem to indicate that the the ESXi host will only communicate VLAN 700 traffic, but I don't have enough experience with vSphere networking to say for sure.
Can you tell me if that is indeed the case? I assume making it a distributed switch would fix the issue if it is? The reason it's not a distributed switch already is that when they set this up they didn't have Enterprise Plus and thus didn't have the option and they do want to eventually migrate to a distributed switch, but I will be able to hasten that if I can confirm that this is the problem. Yeah those 6 machines in the port group would be tagged 700. No matter what you did elsewhere. You could create new port groups, or trunk the vswitch or just untag with 0 I spoke with VMware Tech Support today and got a little lesson on exactly how the vSwitching works.
Those VMs should be on 700 so it is fine that they are tagged that way. Also, I removed authentication from the ports that are configured for other than 700 and they are receiving the correct IP from their respective DHCP pools.
It looks like NPS is doing something to cause all DHCP requests to go to 700. In NPS we have a Network and Connection Request Policy for each VLAN. This uses a regular expression to determine if an incoming request meets the criteria.
We are going to try removing these individual policies and just having a secure wired policy that covers them all and then hopefully they will tag themselves properly based on the access VLAN assigned as quoted in the bullet above from Cisco. That way seems a lot easier and just as secure without having to debug a 100 character regular expression. I'll let you guys know if it works. Thanks so much for all the help thus far.
I've got a Cisco Catalyst 2960 that I'm trying to configure for a remote office with 802.1X wired authentication. The setup I'm going for is Switch ->VoIP Phone via Internal Switch ->PC/Laptop (Domain Joined Win 7/8). Our authentication server is NPS on Windows Server 2008 R2. We are using Snom 300 handsets which do support 802.1X but it's not really feasible for us to configure it on all the handsets, so I've configured the switch to use MAB (MAC Authentication Bypass) for the phones. This for the most part is working brilliantly, the handsets get authenticated and put into the VOICE domain and the VLAN policy is displaying 501, which is our voice VLAN.
But, the phones can still fully access the data VLAN - what am I doing wrong? @JasonSeemann Sure. So when I connect a phone that's been configured for MAB by the RADIUS server (it's sending data-traffic-class=voice and Tunnel-Private-Group-ID = VOICE-LAN to put it on the VOICE domain), if I've configured the phone to use the voice VLAN by ID on the handset itself, it'll access that network fine. But if I don't, it'll carry on using the access VLAN and I'd expect this traffic to be blocked, but it can get DHCP and transfer data just fine. I've tried it with a laptop configured as voice device via MAB and it can access both VLANs at once (get DHCP and transfer data).
– Mar 27 '15 at 8:28. I'm not sure it's the best answer to the question of how to make this work, but in the absence of a better answer, I figured out a way to make it work myself. Basically, I went with the idea that if you are using what is essentially dynamic VLAN assignment (even though it's termed a voice feature), you have to use it for both the VOICE and DATA domains to get the result I was looking for. I changed the access VLAN to a VLAN that doesn't route outside the switch, so in my case switchport access vlan 504 I then modified the policy on our NPS server to pass a VLAN assignment to computers when they authenticate. This has the effect of putting phones or any device MAC spoofing as one without a VLAN configured being put into what is essentially a blackhole network so they can't access anything - but if configured with the correct VLAN ID, they can access the more locked down voice network.
But if a computer is attached and authenticated either directly or via the switch on the phone in the DATA domain, the switch changes the access or native VLAN to our internal network as instructed by the NPS server. This is the result I was looking for - it just meant having to change the config on other switches that make use of the policy server in a more basic form which I was trying to avoid.