Sox Iso 27001 Mapping A Drive
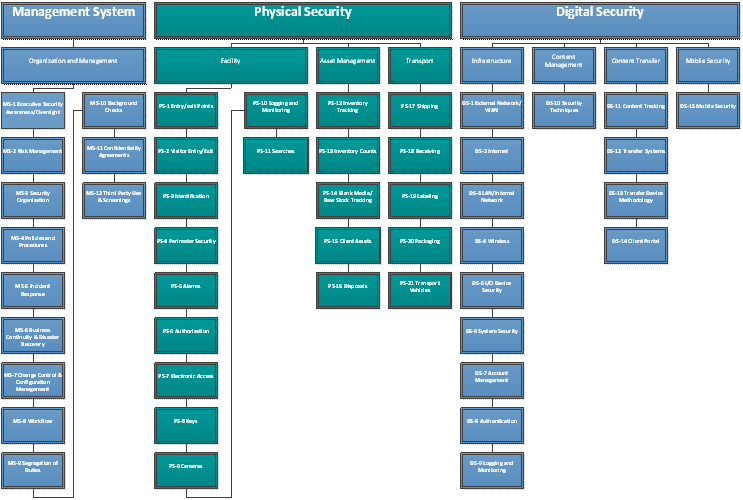
THE ISO/IEC CHALLENGE ISO/IEC Information technology -- Security techniques -- Code of practice for information security controls You might think that implementing an ISO 27002 ISMS program is fairly straight forward, and even an easy sell to the business and supporting enterprise. After all, Information Security is defined by the the C-I-A triad, the most well-known model for security policy development. Who can resist a tried and true C-I-A triad? Install Plugins In Photoshop Portable Mediafire. • Confidentiality, ensuring that information is only accessible to those authorized to have access • Integrity, safeguarding the accuracy and completeness of information and processing methods • Availability, ensuring that authorized users have access to information and associated assets when required Instead of disparaging everyone who resists the full ISO 27002 ISMS implementation, let's empathize with the sheer willpower and perseverance it takes to drive an organization toward this prestigious achievement. Here's a diagram that covers common steps to an ISO 27001 readiness and implementation.
Put simply, it's a lot of work. One area that needn't be difficult, is the thing people often fear the most, the implementation of system policy via security controls. Free Whatsapp Download For Samsung Galaxy Pocket there. What's in it for us?

Mapping Cisco Security Solutions to ISO 27001. ISO/IEC 27001 controls. Hosted by www.anamai.moph.go.th. Iso 27001 iso. RE: ISO 27001 mapping to PCI Craig Wright. Introduction to COBIT for SOX compliance. ISO/IEC is an information security standard that was published in September 2013 It supersedes ISO/IEC, and is published by the International. Mapping between the requirements of ISO/IEC and ISO/IEC.